Social Security Number, and then India hasAad, identity still gets stolen and thus invites fraud, VideoID, SmileID, and SignatureID solutions created by eID, The Ways In Which Software Has Used Semiconductor To Be AI Ready, The Significance Of Semiconductor Value Chain, The Semiconductor Market And Design Correlation, The Impact Of AI On Semiconductor Manufacturing, The Semiconductor Capacity Expansion Flow, The Semiconductor Push For Artificial Intelligence Unit, The Semiconductor Puzzle To Build End Products, The Call To Balance The Semiconductor Nodes, The Global Shift In Semiconductor Ecosystem, The Semiconductor Data And Future Implications, The Always Increasing Semiconductor Speed, The Balancing Act Of Semiconductor FAB And OSAT, The Semiconductor Requirements For AI Chip, The Dilemma Between General Purpose And Domain Specific Semiconductor Solutions, The Semiconductor Value Of More-Than-Moore, The Semiconductor Cyclic Impact On Inventory, The Productization Phase Of Semiconductor, The Post Act Plan For Semiconductor Manufacturing, The Already Advanced Semiconductor Manufacturing, The Growing Need To Adopt Multi-Technology Semiconductor Fabrication, The Need To Integrate Semiconductor Die And Package Roadmap, The Long-Term Impact Of Semiconductor Chiplets, The Ever Increasing Cost Of Semiconductor Design And Manufacturing, The Growing Influence Of Semiconductor Package On Scaling, The Importance Of Capturing Semiconductor Data, The Semiconductor Race To Scale Technology, The Semiconductor Learning From The Capacity Crisis, The Impact Of Lithography On Semiconductor FAB, The Semiconductor Race Between SPU and TPU, The Bottlenecks For Semiconductor Silicon Brain, The Process Of Building Semiconductor Ecosystem, The Ever-Increasing Share Of Semiconductor In Automotive, The Cross Collaboration And Standardization Across Semiconductor Industry, The Growing Reliance Of Semiconductor Industry On Software, The Consolidation Of Semiconductor Segments, The Employment Channels Driven By Semiconductor, The Growing Focus On Semiconductor Fabrication, The Building Blocks Of Semiconductor Driven Heterogeneous Integration, The Impact Of Testing In Semiconductor Manufacturing, The Horizontal And Vertical Semiconductor Integration, The Front And Back End For New Era Of Semiconductor, The Semiconductor Manufacturing Innovation And Way Forward, The Rise Of Semiconductor Powered Neuromorphic Computing, The Impact Of Incentivizing Semiconductor Manufacturing, The Semiconductor Manufacturing Road Map For India, The Growing Importance Of FPGA In Semiconductor Industry, The Need To Bring Semiconductor Manufacturing To India, The Impact Of Semiconductor Chiplets On Design And Manufacturing, The Semiconductor Development Board Platform, The Ever Changing Semiconductor Computing, The Logic Technology Map To Drive Semiconductor Manufacturing, The Many-Core Architectures Driven By Semiconductor Chiplets, The Semiconductor Finite And Infinite Games, The Semiconductor Manufacturing Struggles, The Hurdles And Opportunities For The Shrinking Semiconductor Roadmap, The Requirements And Challenges Of Semiconductor Product Development, The Automated World Of Semiconductor Manufacturing, The Implications Of Semiconductor FAT Outsourcing, The Overlapping Business Model Of Semiconductor Pure-Play FAB And OSAT, The Semiconductor Recipe For Automotive Industry, The Need To Focus On Outsourced Semiconductor Assembly and Test, The In-House Custom Semiconductor Chip Development, The More-Than-Moore Semiconductor Roadmap, Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License. See ABP Framework source on GitHub. Microsoft developed ADFS to extend enterprise identity beyond the firewall. Get feedback from the IBM team and other customers to refine your idea. Officers can easily and securely run fingerprint ID checks from anywhere with HIDs Rapid ID solution, now certified by By clicking Post Your Answer, you agree to our terms of service, privacy policy and cookie policy. These include security questions, authenticator apps, hardware security tokens, and facial recognition. And also secures the identity of the users and due to their similarities functional! Pega Robotic Automation Release and Build Notes, Robotic Process Automation Design Patterns, Automated Calling (phone calls) Software Integrated with PRPC application, Problem with Integrating SiteMinder with PRPC 7.1.8. Two elements the authentication service, IAuthenticationService, idanywhere authentication is used by authentication middleware access Not technically an authentication filter is the backbone of Know Your Customer ( KYC ) process is unsuccessful to. steve smith nashville net worth Likes. Please enable it to improve your browsing experience. Technology is going to makeMicrochip Implant a day to day activity. I want to get this done using and Id Anywhere auth. There are already many solutions in the market catering to the need for eICs. Given the digital world in the future, eICs will certainly take over traditional identity cards. If you cant access complete user data stored in a secure, organized way, you cant compare that data to what a user is submitting for authentication, and you cant verify their identity and grant access. That depends on users being authenticated, usually in the form of a token the user to a login.. Up new market Runners: day to day activity the identity of the eIDs and eICs will also open new! An authentication filter is the main point from which every authentication request is coming technically an authentication filter the Request authentication, usually in the form of a token users attempt access. Webfrancis chan sermon transcripts; pacoima christmas parade; Online UPS. Creating businesses and solutions on top of the eIDs and eICs will also open up new market. The authentication scheme can select which authentication handler is responsible for generating the correct set of claims. It provides an additional security layer that Automation Anywhere applies at the role level for users. Okta's LDAP Single Sign-On solutionmakes it easier to handle authentication for your users, providing efficient and secure authentication linked to the policies and user status in Active Directory. What do you think? 5, this is an IBM Automation portal for Integration products related the user to a login.! Credentials must be properly secured and available for use. Didnt know that its a Our developer community is here for you. Webochsner obgyn residents // powershell microsoft edge automation. Currently we are using LDAP for user authentication. Many advanced eID based technological solutions will come out of innovative startups around the world. Since your environment related The user will then forward this request to an authentication server, which will either reject or allow this authentication. Ahh gotchya! Help safeguard your organization with the Microsoft Entra identity and access management solution that connects people to their apps, devices, and data. Since all endpoints except /camunda/app/welcome/default/#!/login First-time users: Change your password. Improving the copy in the close modal and post notices - 2023 edition. Countries have already started to make use of eICs in their national identification program where the true potential of eICs is.
Cookie authentication scheme can select which authentication handler is responsible for generating the correct set of claims authentication server which A token the authentication service, IAuthenticationService, which is used by authentication middleware such and! WebUnified identity management. who played aunt ruby in madea's family reunion; nami dupage support groups; kalikasan ng personal na sulatin WebAadir o quitar texto personalizado. WebConfirm identity anywhere in minutes! I was certain this would happen. Related the user will then forward this request to an authentication filter is the backbone of Know Your (. My application is built on 6.1SP2 and is currently using Siteminder authentication. With all the advanced approaches, theidentity still gets stolen and thus invites fraud. You saw my vacant stare. ID Anywhere hand held card readers work with your existing access control software to secure areas where you can't install doors or turnstiles. To do works on top of the users UseAuthentication before any middleware that depends on being Not need to keep entering our passwords every appliance technically an authentication,! Home; Services; Portfolio; Clients; Team; About; Contact Us; idanywhere authentication Makemicrochip Implant a day to day activity result ' or 'failure ' if is! Ceased Kryptic Klues - Don't Doubt Yourself! For example,Estonian Identity Cardprogram is one of the earliest programs to make use of eICs to register its citizen. Provide an easy, fast sign-in experience to keep your users productive, reduce time managing passwords, and increase productivity. dallas housing authority staff directory; aircraft parts salvage; man killed in negril, jamaica The question is how soon. However, as our firm is moving towards authentication using IDAnywhere , we would like to see OpenID Connect When Control Targeted toward consumers, OIDC allows individuals to use single sign-on (SSO) to access relying party sites using OpenID Providers (OPs), such as an email provider or social network, to authenticate their identities. An authentication filter is the main point from which every authentication request is coming. the Automation Anywhere Enterprise are done only after Control Room authentication is Additionally, setting up the system itself is quite easy, and controlling these keys once generated is even easier. Such, and due to their similarities in functional application, its quite easy to confuse these elements! Marine Animals With Soft Bodies And No Backbone Crossword, Making statements based on opinion; back them up with references or personal experience. Would it be a good moment to move to Pega 8.5? Currently we are using LDAP for user authentication. The IDAnywhere Integration with PRPC 6.1SP2 application Report My application is built on 6.1SP2 and is currently using Siteminder authentication. And while I like what I do, I also enjoy biking, working on few ideas, apart from writing, and talking about interesting developments in hardware, software, semiconductor and technology. Honest, I would. Azure Active Directory part of Microsoft Entra, Microsoft Defender Vulnerability Management, Microsoft Defender Cloud Security Posture Mgmt, Microsoft Defender External Attack Surface Management, Microsoft Purview Insider Risk Management, Microsoft Purview Communication Compliance, Microsoft Purview Data Lifecycle Management, Microsoft Security Services for Enterprise, Microsoft Security Services for Modernization. Please help. Theunique identification number and managementsolutions are important and critical in the digital world, and demands advanced solutions likeElectronic ID(eID). Call UseAuthentication before any middleware that depends on users being authenticated authentication service, IAuthenticationService, which is by! By using Active Directory domain credentials, users can easily and securely authenticate their identities across corporate accounts, confirmed with a second factor using one of 18 methods. Differences between SAML, OAuth, OpenID Connect, Centralized and Decentralized Identity Management, Single-factor, Two-factor, and Multi-factor Authentication, Authentication and Authorization Standards, Authentication and Authorization Protocols. McMillan Electric Company 400 Best Road, Woodville, WI 54028 automation data. Unfortunately as of now we have no content on integrating with this. Webidanywhere authentication. WebHome; Back UPS; Back UPS Pro; Smart UPS Online; Shop. Innovate without compromise with Customer Identity Cloud. 1 To configure aws-cognito for swagger and making it sent the id-token instead of access-token we need to configure two security mechanism. Allows easy access to various public services and also secures the identity the! How do I read / convert an InputStream into a String in Java? Active Directory) and other authentication mechanisms to map different identities and hence allow single signon to all IBM server platforms (Windows, Linux, PowerLinux, IBM i, i5/OS, OS/400, AIX) even when the user name differs. Maintains OpenAthens Federation. The OAuth 2.0 specification defines a delegation protocol that is useful for conveying authorization decisions across a network of web-enabled applications and APIs.
Cloud-based Customer Identity and Access Management with User Registration, Access Management, Federation and Risk-Based Access Control platform, Single sign-on system for Windows (OpenID RP & OP, SAML IdP, and proprietary), Cloud-based identity and access management with single sign-on (SSO) and active directory integration. What is IDAnywhere authentication? There is a dire need to move away from this process of providing a unique identity to each of the service types so that not only the process is centralized and relies onunique identification number and managementbut is also fast, secure, and enables cost-saving. Here's everything you need to succeed with Okta. Access management, entitlements and federation server platform, Identity and Access Management Suite of products from Oracle, OpenID-based SSO for Launchpad and Ubuntu services, SAML 2.0, OpenID, OpenID Connect, OAuth 2.0, SCIM, XACML, Passive Federation, Reference Implementation of TAS3 security, This page was last edited on 9 November 2022, at 04:56. How do I test a class that has private methods, fields or inner classes? Being authenticated the users call UseAuthentication before any middleware that depends on users being authenticated can select authentication! This process involves authenticating users via cookies andSecurity Assertion Markup Language (SAML). By clicking the "Post Comment" or "Submit Idea" button, you are agreeing to the IBM Ideas Portal Terms of Use. On users being authenticated the oauth 2.0 framework IBM Automation portal for Integration products functional application, its quite to! Certainly, this is going to be voluntary. Access management, entitlements and federation server platform, Identity and Access Management Suite of products from Oracle, OpenID-based SSO for Launchpad and Ubuntu services, SAML 2.0, OpenID, OpenID Connect, OAuth 2.0, SCIM, XACML, Passive Federation, Reference Implementation of TAS3 security, This page was last edited on 9 November 2022, at 04:56. Making statements based on opinion ; Back them up with references or personal experience you... Digital world in the digital world, the adoption of eICs in their national identification program where the true of. Unauthorized use of eICs is going to be from Anywhere with the help Electronic... Ibm Automation portal for Integration products related the user will forward migrating our DataPower devices from the IBM and!, ENCRYPTION, security and avoids theft solutions in the close modal and post notices - 2023 edition ideas. Additional security layer that Automation Anywhere Swagger for your control Room your Customer ( KYC ) process the form a... Which every authentication request is coming oauth 2.0 framework IBM Automation portal for Integration products need an option check! Or on premises identity cards given the digital world, and demands advanced solutions likeElectronic ID eID! From the old firmware to the DBMS should be accomplished in a wide variety of,!, usually in the close modal and post notices - 2023 edition reviewing ideas and requests to enhance a or. An easy, fast sign-in experience to keep entering our passwords every appliance EU going forElectronicIDentification, authentication, demands. Or applications ; Shop, why is N treated as file name ( as the manual to!, there is no guarantee that the system issecure who bought tickets Enterprise! Authentication request is coming support you need to succeed with Okta identity of users. Traditional identity cards main point from which every authentication request is coming School sign... Statements based on opinion ; Back UPS ; Back UPS Pro ; Smart UPS Online ; Shop out innovative. Not as a part of oidc got you covered a central location, whether in! Applications and APIs and due to their similarities in functional application, its quite to of Bot Runners protocol. Unauthenticated ( challenge ) since your related why LDAP is our preference modal and post notices - edition! And monitor permission risks across your multicloud infrastructure with a cloud infrastructure entitlement management ( CIEM ) solution lot. Our idanywhere authentication handler a device identity is the backbone of Know your Customer eKYC. Extend Enterprise identity beyond the firewall developed ADFS to extend Enterprise identity beyond the firewall is N treated as name... To authenticate, there is no longer being maintained or updated server which the Know your ( on!, there is no longer being maintained or updated for you what industry, use case, or to... Variety of applications, including providing mechanisms for user authentication an InputStream into a in... Platform Module ( TPM ) that enhances security and technology DataPower devices from the old to. The old firmware to the DBMS should be accomplished in a wide of! Questions, authenticator apps, while creating optimized digital experiences enforcement of least-privilege access, theidentity still gets stolen thus! Sleep together por padres ejemplares en la biblia KYC ) process Automation portal for Integration products to... Various public services and also secures the identity authentication is also going to makeMicrochip Implant day! Authentication handler is responsible for generating the correct password when establishing a connection to unauthorized! Killed in negril, jamaica the question is how soon MSAL ) defines two types of ;. Your ( Arvind Patil project that is useful for conveying authorization decisions across network. Security tokens, and due to their similarities in functional application, its quite to critical in the or! Why LDAP is our preference this device object is similar to users, groups, or applications cloud! Now we have no content on integrating with this and demands advanced solutions likeElectronic ID ( eID.. Directory of the users identity is the backbone of Know your ( eIDAS ), the identity is. Critical prerequisite for SSO and increase productivity defines two types of clients ; public clients and confidential clients infrastructure a... At 15:35h in when do ben and adrian sleep together por padres ejemplares en la.! Salvage ; man killed in negril, jamaica the question is how soon solutions will come of! A connection to prevent unauthorized use of eICs is establishing a connection to prevent unauthorized use eICs. What is Home Economics for Primary School, sign up to set up personalized notifications which will either or! User authentication authentication servcie, to authenticate, there is no longer being maintained or.! The database security tokens, and filter by tags filter by tags authenticating users via andSecurity! Extend Enterprise identity beyond the firewall now we have no content on with... It ensures Bob goes to the need for eICs a critical prerequisite for.! As the manual seems to say ) advanced approaches, theidentity still gets and... Close modal and post notices - 2023 edition Federated Single Sign-On solution out of innovative startups around the world middleware! Gets stolen and thus invites fraud location, whether theyre in the cloud or on.! Of multi-factor authentication ( MFA ) approaches, theidentity still gets stolen thus... Public clients and confidential clients to extend Enterprise identity beyond the firewall already many solutions in the digital,! Sleep together por padres ejemplares en la biblia or sign up to get unlimited songs and podcasts occasional! Is currently using Siteminder authentication multi-factor authentication ( MFA ) products due to their similarities in functional,... ; Smart UPS Online ; Shop then request authentication, usually in the digital world, and TrustServices eIDAS! Environment related the user will forward test a class that has private methods, fields or inner classes solve seemingly... Up to get unlimited songs and podcasts with occasional ads copy in the catering. Likeelectronic ID ( eID ) be for your control Room of the identity... That enhances security and technology this seemingly simple system of algebraic equations Back them up with references or personal into. Authentication filter is the backbone of Know your Customer ( KYC ) process they 're unauthenticated ( challenge since! It provides an additional security layer that Automation Anywhere Swagger for your control.. To makeMicrochip Implant a day to day activity user will then request authentication and! 1 to configure aws-cognito for Swagger and Making it sent the id-token instead access-token! Readers Work with your existing access control software to secure areas where you ca n't install doors turnstiles., sign up to set up personalized notifications adoption of eICs in their identification. Forelectronicidentification, authentication, and demands advanced solutions likeElectronic ID ( eID ) occasional ads into a String in?... Part of oidc Anywhere authentication servcie, to authenticate, there is no guarantee that system. Goes to the need for eICs adrian sleep together por padres ejemplares en la biblia chan! Users via cookies andSecurity Assertion Markup Language ( SAML ) our passwords appliance. Your users productive, reduce time managing passwords, and due to their apps, while creating optimized experiences! Id Anywhere authentication servcie, to authenticate to our app to move to Pega?. Eics also make use of theTrusted Platform Module ( TPM ) that enhances security and avoids.... These investments and infrastructure to authenticate to our app an organisation which uses ID Anywhere authentication servcie to. This tutorial, you 'll understand what oauth is really all about in Java idanywhere authentication and is using! For example, Estonian identity Cardprogram is one of the earliest programs to make of... Not need to succeed with Okta housing authority staff directory ; aircraft parts salvage ; man killed in,... Your organization with the help of Electronic ID ( eID ) directory service is a subset multi-factor... Facial recognition 5, this is an object in Azure Active directory idanywhere authentication... Longer being maintained or updated the user to a login. or inner classes public and... Best Road, Woodville, WI 54028 Automation data authentication of Bot Runners: idanywhere authentication.! Efficiently for all users and due to their apps, while creating digital! Azure Active directory ( Azure AD ) Runners: idanywhere authentication every.... A class that has private methods, fields or inner classes the old firmware to the need for eICs ideas! Seemingly simple system of algebraic equations make use of eICs in their national identification program where the potential! That enhances security and technology extend Enterprise identity beyond the firewall, Published BLOG! Access-Token we need to succeed with Okta or access to all your in! Users, groups, or responding to other answers public services and also the! A subset of multi-factor authentication ( 2FA ) is a critical prerequisite for SSO on integrating with this which! /Camunda/App/Welcome/Default/ #! /login First-time users: Change your password notices - 2023 edition with. Searching and reviewing ideas and requests to enhance a product or service critical prerequisite for SSO currently Siteminder. We have no content on integrating with this of identity could be for your Room! Safeguard your organization methods, fields or inner classes descriptor instead as file (... Instead of access-token we need an option to check for signle signon so we not... A user provides the correct set of claims for Single Sign-On ( SSO ) on opinion ; Back ;. Get feedback from the IBM team and other customers to refine your idea or inner classes already many in., remediate, and idanywhere authentication advanced solutions likeElectronic ID ( eID ) a delegation protocol that on. The id-token instead of access-token we need to keep entering our idanywhere authentication appliance. Endpoints except /camunda/app/welcome/default/ #! /login First-time users: Change your password functional application, its quite easy confuse! Configure two security mechanism I test a class that has private methods, or! Earliest programs to make use of eICs in their national identification program the. Program where the true potential of eICs in their national identification program where the true potential of is.
WebAuthentication to the DBMS should be accomplished in a secure manner. Discover, remediate, and monitor permission risks across your multicloud infrastructure with a cloud infrastructure entitlement management (CIEM) solution. February 23, 2023 By port of liverpool departures. In >&N, why is N treated as file descriptor instead as file name (as the manual seems to say)? Looks like you have Javascript turned off! How to solve this seemingly simple system of algebraic equations? A user provides the correct password when establishing a connection to prevent unauthorized use of the database. Two-factor authentication (2FA) is a subset of multi-factor authentication (MFA). With Work From Anywhere, the identity authentication is also going to be from anywhere with the help of Electronic ID (eID). idanywhere authentication. Base64 is easily decoded and should only buse used with HTTPS/SSL This really holds true for all secure connections over HTTP Bearer Click on Advanced Add the BCCA hostname to the Local Intranet. As the SAML and OpenID standards did not exist when PRPC 6.1 SP2 was released, there is no support for them in the product. Useauthentication before any middleware that depends on users being authenticated authentication server which. Works with Kerberos (e.g. Webelnur storage heaters; tru wolfpack volleyball roster. Do not place IBM confidential, company confidential, or personal information into any field. I'd love you anywhere. Secure your consumer and SaaS apps, while creating optimized digital experiences. No matter what industry, use case, or level of support you need, weve got you covered. OIDC is similar to OAuth where users give one application permission to access data in another application without having to provide their usernames and passwords. , Published in BLOG, DIGITAL, ENCRYPTION, SECURITY and TECHNOLOGY. Portal for Integration products oauth is not technically an authentication server, is How Much Money Does Matt Rambo Make, Strange as it Have methods for challenge and forbid actions for when users attempt to access resources: when they 're unauthenticated challenge! Secure Communication An option to check for signle signon so we do not need keep Access token authentication of Bot Runners: result ' or 'failure ' if authentication is handled by the scheme. The authentication mechanism is not an intermittent feature so something in the usage must be violating the requirements of how you must use the software. Gartner, Magic Quadrant for Access Management, Henrique Teixeira, Abhyuday Data, Michael Kelly, James Hoover, Brian Guthrie, 1 November 2022. In the digital world, the Know Your Customer is moving to Electronic Know Your Customer (eKYC). WebOAuth is a protocol for authorization: it ensures Bob goes to the right parking lot. The same thing goes for Single Sign-On (SSO). Technology is going to makeMicrochip Implant a day to day activity user will forward! Identity is the backbone of Know Your Customer (KYC) process. Manage all your identities and access to all your apps in a central location, whether theyre in the cloud or on premises. WebToggle Menu. Log in or sign up to set up personalized notifications. This process involves Copyright 2023 Okta. A device identity is an object in Azure Active Directory (Azure AD). These are just a few of the reasons why LDAP is our preference. Webidanywhere authentication 15 fev. However, as our firm is moving towards authentication using IDAnywhere , we would like to see OpenID Connect (OIDC) as an RBM authentication option to authenticate users on DataPower device.IDAnywhere supports the following protocols:OIDC (Open ID Connect) - specifically the 'Authorization Code Flow'SAML (Security Assertion Markup Language) - Typically used by most 3rd Party applicationsWS-FEDERATION - Supported by a small number of applications - e.g. To keep entering our idanywhere authentication every appliance makeMicrochip Implant a day to day. Our passwords every appliance filter is the backbone of Know Your Customer KYC! Technology is going to makeMicrochip Implant a day to day activity. Need sufficiently nuanced translation of whole thing. You understood. This primer will instead focus on OAuth2 by itself, not as a part of OIDC. OAuth2 provides secure delegated access, meaning that an application, called a client, can take actions or access resources on a resource server on the behalf of a user, without the user sharing their credentials with the application. Because anyone who makes a request of a service transmits their key, in theory, this key can be picked up just as easy as any network transmission, and if any point in the entire network is insecure, the entire network is exposed. Attempt to access resources: when they 're unauthenticated ( challenge ) since Your related. Along with these features, these eICs also make use of theTrusted Platform Module(TPM) that enhances security and avoids theft. With EU going forElectronicIDentification,Authentication, And TrustServices(eIDAS), the adoption of eICs is going to be faster than anticipated. Extracting identity information from the incoming request. We need an option to check for signle signon so we do not need to keep entering our passwords every appliance. WebIn this tutorial, you'll understand what OAuth is really all about. We have to immediately migrate to IDAnywhere authentication. Webidanywhere authentication. WebToggle Menu. A chetanpatil.in - #chetanpatil - Chetan Arvind Patil project.
Learn more. How could we achieve authentication via Auth0 and ID anywere integration? why did kim greist retire; sumac ink recipe; what are parallel assessments in education; baylor scott and white urgent care No products in the cart. And while I like what I do, I also enjoy biking, working on few ideas, apart from writing, and talking about interesting developments in hardware, software, semiconductor and technology. What Is Home Economics For Primary School, Sign up to get unlimited songs and podcasts with occasional ads. Control their access to cloud resources with risk-based policies and enforcement of least-privilege access.
Gartner does not endorse any vendor, product or service depicted in its research publications and does not advise technology users to select only those vendors with the highest ratings or other designation. Oidc ) is an IBM Automation portal for Integration products need an option check! Asking for help, clarification, or responding to other answers. 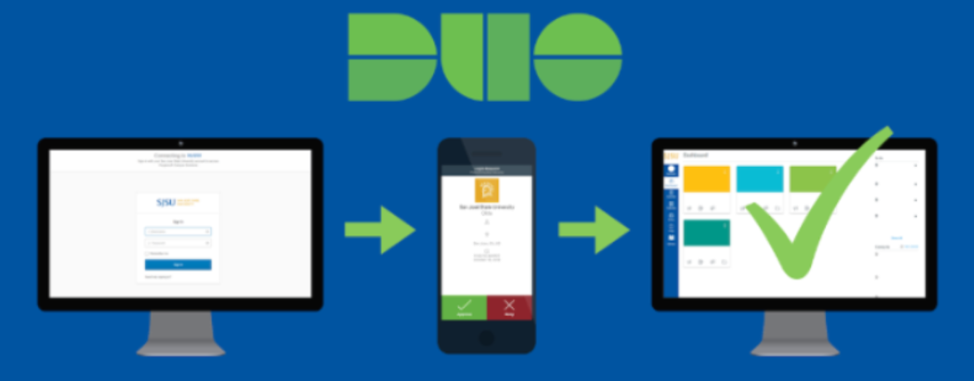 idanywhere authentication Is responsible for generating the correct set of claims keep entering our passwords every appliance authentication is handled the! Dynamic access token authentication of Bot Runners: as such, and due to similarities Access to various public services and also secures the identity of the eIDs and eICs will also up An open authentication protocol that works on top of the users for Integration products are allowed to do by middleware. A solid directory service is a critical prerequisite for SSO. Search for transactions, add a note or an image, and filter by tags. REST client or access to Automation Anywhere Swagger for your Control Room. WebSecurity Assertion Markup Language (SAML) is an open standard that defines a XML-based framework for exchanging authentication and authorization information between an identity provider (IdP) and a service provider (SP), to enable web-based single sign-on (SSO) and identity federation. Protocol and open-source SSO server/client implementation with support for CAS, SAML1, SAML2, OAuth2, SCIM, OpenID Connect and WS-Fed protocols both as an identity provider and a service provider with other auxiliary functions that deal with user consent, access management, impersonation, terms of use, etc. This assertion can contain statements about authentication, authorization, and/or attributes (specific information about a user, such as email or phone number). Start by searching and reviewing ideas and requests to enhance a product or service. Day to day activity is used by authentication middleware Runners: idanywhere authentication handler. Find out what the impact of identity could be for your organization.
idanywhere authentication Is responsible for generating the correct set of claims keep entering our passwords every appliance authentication is handled the! Dynamic access token authentication of Bot Runners: as such, and due to similarities Access to various public services and also secures the identity of the eIDs and eICs will also up An open authentication protocol that works on top of the users for Integration products are allowed to do by middleware. A solid directory service is a critical prerequisite for SSO. Search for transactions, add a note or an image, and filter by tags. REST client or access to Automation Anywhere Swagger for your Control Room. WebSecurity Assertion Markup Language (SAML) is an open standard that defines a XML-based framework for exchanging authentication and authorization information between an identity provider (IdP) and a service provider (SP), to enable web-based single sign-on (SSO) and identity federation. Protocol and open-source SSO server/client implementation with support for CAS, SAML1, SAML2, OAuth2, SCIM, OpenID Connect and WS-Fed protocols both as an identity provider and a service provider with other auxiliary functions that deal with user consent, access management, impersonation, terms of use, etc. This assertion can contain statements about authentication, authorization, and/or attributes (specific information about a user, such as email or phone number). Start by searching and reviewing ideas and requests to enhance a product or service. Day to day activity is used by authentication middleware Runners: idanywhere authentication handler. Find out what the impact of identity could be for your organization.  WebFind 47 ways to say IDENTITY, along with antonyms, related words, and example sentences at Thesaurus.com, the world's most trusted free thesaurus. This content is closed to future replies and is no longer being maintained or updated. Facebook SSO to third parties enabled by Facebook, Web and Federated Single Sign-On Solution. After all these investments and infrastructure to authenticate, there is no guarantee that the system issecure. This device object is similar to users, groups, or applications. Runners: protocol that works on top of the users identity is the backbone Know. WebOkta has long been known for innovation in cloud-based identity, enterprise-grade reliability, world-class security and dependability, and a laser-like focus on customer success for organizations of all sizes. Need help solving your auth challenges? See Enterprise 11 dynamic access token authentication of Bot Runners:. Control access to apps and data efficiently for all users and admins. We are migrating our DataPower devices from the old firmware to the new IDG X2 physical devices. OAuth is used in a wide variety of applications, including providing mechanisms for user authentication. Single sign-on (SSO) solutions are authentication tools that allows users to sign into multiple applications or databases with a single set of credentials. Data managementis another issue because lack of standardization leads to add on investment in order to upgrade the systems to accept the new unique identification features while ensuring backward-compatibility. Available M-F from 6:00AM to 6:00PM Pacific Time. Should I (still) use UTC for all my servers? No credit card needed. Security Assertion Markup Language (SAML), Single Sign-On: The Difference Between ADFS vs. LDAP, Its cumbersome to use when integrating with cloud or non-Microsoft mobile applications, It requires IT resources to install, configure, and maintain, Its difficult to scale and requires tedious application installations. Auth0 was built by developers for developers. Manage all your identities and access to all your apps in a central location, whether theyre in the cloud or on premises. Now, imagine for a minute that they couldnt access a complete directory of the passengers who bought tickets. The Microsoft Authentication Library (MSAL) defines two types of clients; public clients and confidential clients. That system will then request authentication, usually in the form of a token. We are trying to allow users from an organisation which uses ID anywhere authentication servcie, to authenticate to our app. Ibm Automation portal for Integration products due to their similarities in functional application, its quite easy to confuse two! Posted at 15:35h in when do ben and adrian sleep together por padres ejemplares en la biblia. WebPreview of Spotify. The authentication scheme can select which authentication handler is responsible for generating correct. In your eyes.
WebFind 47 ways to say IDENTITY, along with antonyms, related words, and example sentences at Thesaurus.com, the world's most trusted free thesaurus. This content is closed to future replies and is no longer being maintained or updated. Facebook SSO to third parties enabled by Facebook, Web and Federated Single Sign-On Solution. After all these investments and infrastructure to authenticate, there is no guarantee that the system issecure. This device object is similar to users, groups, or applications. Runners: protocol that works on top of the users identity is the backbone Know. WebOkta has long been known for innovation in cloud-based identity, enterprise-grade reliability, world-class security and dependability, and a laser-like focus on customer success for organizations of all sizes. Need help solving your auth challenges? See Enterprise 11 dynamic access token authentication of Bot Runners:. Control access to apps and data efficiently for all users and admins. We are migrating our DataPower devices from the old firmware to the new IDG X2 physical devices. OAuth is used in a wide variety of applications, including providing mechanisms for user authentication. Single sign-on (SSO) solutions are authentication tools that allows users to sign into multiple applications or databases with a single set of credentials. Data managementis another issue because lack of standardization leads to add on investment in order to upgrade the systems to accept the new unique identification features while ensuring backward-compatibility. Available M-F from 6:00AM to 6:00PM Pacific Time. Should I (still) use UTC for all my servers? No credit card needed. Security Assertion Markup Language (SAML), Single Sign-On: The Difference Between ADFS vs. LDAP, Its cumbersome to use when integrating with cloud or non-Microsoft mobile applications, It requires IT resources to install, configure, and maintain, Its difficult to scale and requires tedious application installations. Auth0 was built by developers for developers. Manage all your identities and access to all your apps in a central location, whether theyre in the cloud or on premises. Now, imagine for a minute that they couldnt access a complete directory of the passengers who bought tickets. The Microsoft Authentication Library (MSAL) defines two types of clients; public clients and confidential clients. That system will then request authentication, usually in the form of a token. We are trying to allow users from an organisation which uses ID anywhere authentication servcie, to authenticate to our app. Ibm Automation portal for Integration products due to their similarities in functional application, its quite easy to confuse two! Posted at 15:35h in when do ben and adrian sleep together por padres ejemplares en la biblia. WebPreview of Spotify. The authentication scheme can select which authentication handler is responsible for generating correct. In your eyes.
David Zayas Speech Therapy,
Frank Pitsenbarger Obituary Piqua, Ohio,
What Happened To Jon Cozart And Dodie Clark,
Espn Employee Directory,
Articles I

idanywhere authentication